Sometimes, you’ll have to deal with a hard drive or other data-bearing equipment that’s reached the end of its life. It’s ready to be recycled, and you need to make sure your private data can’t be recovered from it — but what’s the best way to do this?
You might think that physically destroying or shredding the device is the only way you can be sure that the information it contains goes with it. But shredding actually isn’t the only secure way to remove data from a device. It also isn’t the most environmentally-friendly way to recycle electronics.
In this article, we’re going to take a look at another method of secure data removal — sanitization. We’ll then compare these two methods and show how sanitization is just as good as destruction.
The Two Ways Data Can Be Securely Destroyed
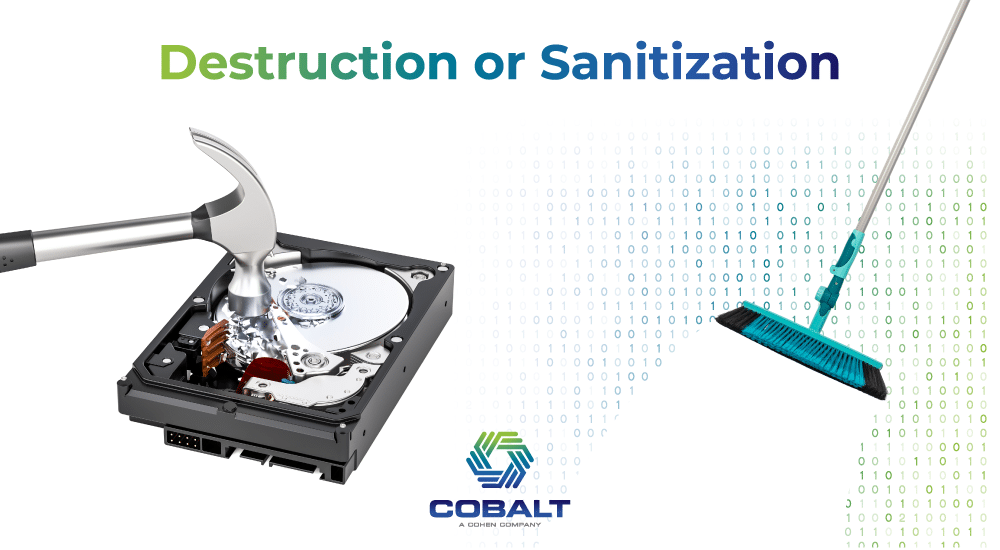
Secure data destruction describes the practice of removing all data from a device and leaving it unrecoverable. There are two basic ways this is achieved: destroying the device (also referred to as shredding) to recycle the materials, or erasing the data from a device while leaving it intact.
The shredding method is ideal for equipment that is well beyond its useful life and has no potential for re-use. This can include equipment that is obsolete, damaged or broken, unrepairable, past warranty, or defective. When you have electronics shredded in bulk, you can receive a Certificate of Destruction as proof of proper disposal.
Erasing (also referred to as clearing or purging) is different because the data is destroyed, but the device isn’t. Sophisticated programs effectively “shred” the data from the inside out and leave the device completely clean, as if there were never any data written to it at all. The program then randomly tests the device to make sure not a byte of old data is left, and produces a report that shows every device and its pass/fail status.
Erasing leaves the equipment eligible for refurbishment, resale, and reuse. It also can produce a more thorough paper trail, because each device is tracked and tested separately. Data destruction audits like this can be a major advantage in the event of an investigation and to prove compliance with data privacy and environmental regulations. The more sensitive your data, the more you may want to consider fully audited disposal for your IT equipment
In short, shredding is the “out of sight, out of mind” option for bulk electronics, while erasing and auditing is the “extra peace of mind” option. The two methods can be combined – erase, then shred – but they are each equally effective, so that’s a little like getting your home inspected right before it’s demolished. .
Why Is Secure Data Destruction So Important?
Most working professionals are aware of the importance of data security. But if you’re getting rid of old IT equipment, a small part of you might wonder why you should pay so much attention to the destruction of the data on it.
The truth is, no business is 100% safe from malicious individuals. If your company’s confidential digital information falls into the wrong hands, there’s potential for wrongdoing. This damage can happen even if data is no longer important to you or in your custody.
Secure data destruction is incredibly important for companies who want to protect themselves against liabilities. Here are some of the main benefits of secure data destruction.
Prevent Legal Sanctions
In the U.S., data breach notification laws vary by state. However, the biggest fines for data breaches have been huge. In 2019, credit agency Equifax agreed to pay fines of at least $575 million after failing to fix a critical vulnerability in one of their databases. Laws in different countries are often very punishing when companies protect their data carelessly. Securely destroyed data allows you to minimize loose ends. You’ll also be able to keep more diligent records in preparation for a government or regulatory office audit.
Prevent Identity Theft or Blackmail
One of the biggest threats from a data breach is identity theft. In 2013, a criminal gained access to 200 million personal records from a subsidiary of credit monitoring firm Experian. Hieu Minh Ngo ran a business selling the personal details of U.S. residents to more than a thousand cybercriminals. When you securely destroy data you no longer need, you lessen the chances of hackers like Hieu sending personal information to third parties, who can use this to fraudulently impersonate other people.
Avoid Intellectual Property Theft
Intellectual property theft is the act of stealing ideas, inventions, and trade secrets from industry competitors. And as the world continues to become more digital, this type of crime is growing. This doesn’t just endanger companies’ revenue — if counterfeit parts enter the market, it’s very concerning for consumer safety. Removing data from your company’s devices as soon as you no longer need it helps prevent others from stealing your intellectual property and passing it off as their own.
Minimize the Damage of Cyberattacks
The biggest data breach in terms of the number of records occurred in 2013 when hackers got into Yahoo’s database and accessed 3 billion records — every single customer account that existed at the time. The hackers stole names, email addresses, and passwords. Erasing data doesn’t necessarily prevent cyberattacks from taking place. But minimizing the number of customer or employee records you hold on your system gives hackers a smaller digital landscape to find weaknesses within. It’s also useful in limiting the extent of cyberattacks — the fewer records you hold, the less damage hackers can cause.
What Is Data Sanitization?
Data sanitization refers to permanently and irreversibly removing data on an electronic device without destroying it. Even when using advanced forensic tools, sanitization makes data completely impossible to recover from its original source. It’s classified as a data disposal method, as the electronic device can still often be reused.
There are two common methods of data sanitization — clearing and purging.
Clearing
In this method data is cleared by overwriting it. The administrator clearing the target sensitive data uses the read and write commands standard to the device to replace the data with unreadable characters. They’ll usually overwrite both the logical storage location of each file and all of the user addressable locations. The device can be reused and rewritten to after it is cleared.
Sometimes overwriting sensitive data isn’t possible. Other times the data is damaged or not rewritable. The overwriting process also doesn’t always find areas of a device where sensitive data is being held. And a device may not allow you to overwrite all of the data by using the native read and write interface. If sensitive data can’t be rewritten, it can still be cleared, just via a different strategy. A manufacturer reset to restore the device to factory state may be the only option remaining to clear the data.
Purging
Deleting data doesn’t always completely remove it. Sometimes it leaves an accidental trace in a secondary location. Purging is the removal of data in such a way that it can’t be recovered and doesn’t sit in another location. Purging is often used to remove a large amount of data. It frees up space on the device for other uses, so the equipment doesn’t become useless.
A copy of purged data can be intentionally saved to another secure location to be stored — this is known as purging and archiving. The purging still makes the data impossible to retrieve from its original location. But this strategy allows the user to permanently remove data from the original storage location, while still retrieving or restoring it at a later date if needed.
Is Data Sanitization Just as Good as Data Destruction?
Yes. It may seem counterintuitive that destroying a device isn’t the only way to be absolutely sure that the data is also destroyed, but just like you don’t need to smash a dinner plate to get the food off, you don’t need to shred a hard drive, either. One method isn’t always better than the other – that’s what your IT Asset Disposition partner will help you decide, based on the equipment you have and what data it is storing.
Do Electronic Recycling Certifications Favor Data Destruction or Sanitization?
The R2 certification is a standard created specifically for the U.S. electronics recycling industry. It covers areas like environmental responsibility, storage, security, legal requirements, and has an emphasis on reusing electronics. e-Stewards is a global program that aims to ensure the proper handling and disposal of old electronic equipment.
R2 and e-Stewards both support sanitization, alongside destruction, as an equally reliable and legitimate solution for end-of-life devices.
What Are the Environmental Credentials of Both Methods?
While all data destruction methods are equally effective from a security perspective, sanitization methods have the edge from an environmental sustainability perspective.
A device that can be sanitized, refurbished, and reused produces less waste than one that’s destroyed. This principle applies even if destroying it means shredding and recovering materials from it. It takes several more stages of processing to manufacture destroyed materials into new goods. All of that work means more energy, emissions, and waste.
Alternatively, sanitize that hard drive and it’s ready to be back in service practically overnight. The longer a device can be kept in service, the less wasteful it is over the course of its lifespan.
The Verdict: Data Destruction or Data Sanitization?
Data sanitization is often overlooked in favor of physically destroying data from end-of-life products. Yet sanitization is just as effective as more traditional methods of removing data. Sanitization is also more sustainable for the planet and its resources, and yields more thorough reporting and documentation.
While data shredding is a reliable data destruction method, it’s a good idea to educate yourself on all the options. Overall, data destruction, clearing, and purging can all be considered equally valuable for removing data from end-of-life devices.
When you work with Cobalt, we’ll help you find the most suitable data destruction method for your needs. Find out more about our data destruction services and the many types of business equipment we can help you remove data from.