What do you do when you unexpectedly come across someone else’s personal information?
I recently bought a used car, a Hyundai hybrid, to replace my well-loved Toyota hatchback that I’d had since 2010. Despite the Hyundai only being three years newer than the Toyota, it came with a LOT more bells and whistles – which just goes to show you how fast technology changes and what we became accustomed to in such a short time.
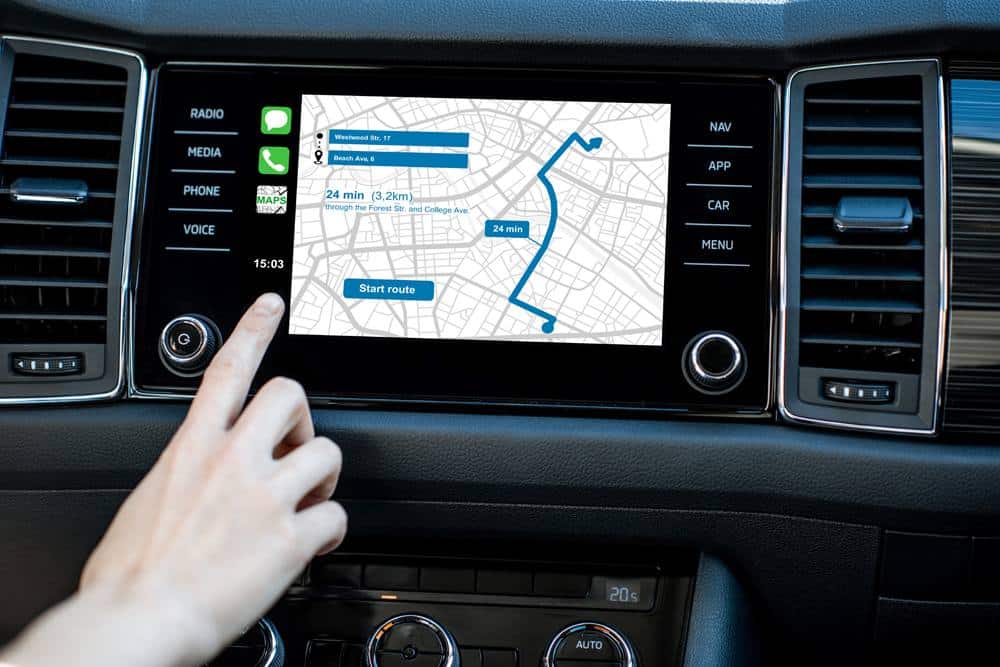
After nearly ten years of having to manually plug in my phone to the hatchback’s audio if I wanted music or driving directions, the built-in Bluetooth and onboard navigation was a big jump forward, and I was excited to give it a try.
When I went to add my home and work addresses into the computer’s address book, though, I found myself looking at the previous owner’s home address instead. She hadn’t cleared her personal information from the car before selling it to the shop I bought it from, and neither had the shop. All of her navigation history was also stored under the “recent places” menu.
How do I know the last owner was a woman? Well, I had also found her old registration tag in the glove box when putting my insurance card away.
Before I had any exposure to the IT asset disposition industry, I probably would not have thought much of this discovery. But since learning more about the risks of leftover data on old hard drives that go on to new owners, or those that get recycled, this gave me pause.
Imagine I were a person with bad intentions and poor impulse control. Stumbling on this information just gave me an opportunity, and a target. Not only do I have this person’s name and home address, at the tap of a screen, the car would literally take me right to her front door!
A sketchy person could also use that information to find out more about her – for example, looking her up on social media, finding out where she works, or digging up details on her family. It takes little effort, skill, or time to uncover a LOT about a person in the internet age.
A decent person would destroy the document and delete the old addresses – which is exactly what I did. But this experience is a pointed reminder of the risks we unknowingly leave ourselves exposed to when we say goodbye to our old electronics.
More and more everyday products are being embedded with internet-ready technology. While it’s pretty slick to be able to lock your doors, turn lights on and off, send money to friends, and start your car from your smartphone, there’s a tradeoff to all this connectivity that is never clearer than the moment that device leaves your hand.
Working at Cobalt, I’m familiar with the risks of handling old IT assets improperly. But this firsthand experience will definitely stick with me and have me thinking even more carefully about where my data goes when I’m not looking.